Friday, September 9, 2016
Tuesday, September 6, 2016
Aerohive ID Manager (IDM) private pre shared key (PPSK), how does it work ?
Aerohive IDM is a AAA server, it use radsec protocol. Usually if you authenticate against a AAA server like RADIUS the users need to enter a username and password,
Whats interesting with Aerohive PPSK+IDM is that you can create a PSK (WPA2-Personal) SSID and provide PSK per user. And these PSKs can be authenticated against a PSK list in IDM, so how does this work ?

For this the SSID should be configured in the HiveManager as below,


Lets say you pushed this configuration to 3 access points or more, two of the access points will become IDM proxy. All the access points talk to IDM through the two APs which are elected to be the radsec proxy,

Lets say the client is connecting to the AP with hostname AH-016e80 (172.16.1.55), how does the authentication pkts flow through ? AH-016e80 (172.16.1.55) communicate to AH-0168c0 (172.16.1.56) using RADIUS and AH-0168c0 (172.16.1.56) autheticate the user with IDM using radsec ,
client --- AH-016e80 (172.16.1.55) ----- RADIUS ---- AH-0168c0 (172.16.1.56) --- radsec ----IDM
Pkt capture : https://drive.google.com/open?id=0B3ctVg8ubiwUdmd0T0FKM0Z2S2M
Pkt capture : Client --- AH-016e80 (172.16.1.55)

Pkt capture : AH-016e80 (172.16.1.55) ----- RADIUS ---- AH-0168c0 (172.16.1.56)

Pkt capture : AH-0168c0 (172.16.1.56) --- radsec ----IDM

How would you see this process in Aerohive _debug messages,
_debug auth all
Tech data : https://drive.google.com/open?id=0B3ctVg8ubiwUX0YySndaOElWMnM
---- First connection log @ AH-016e80 (172.16.1.55) -----
[auth_info]: received EAPOL-Key frame (4/4 Pairwise)
[auth_info]: sending 3/4 msg of 4-Way Handshake
[auth_basic]: Obtain PPSK PMK: 451F***
[auth_basic]: Query PPSK success for sta 286a:ba44:1de4, username: ruwanindika+user2@gmail.com, session-timeout:
notice ah_auth: authentication OK, username '28-6A-BA-44-1D-E4', service (unknown)
[auth_basic]: Sending PPSK request to external server for sta 286a:ba44:1de4
[auth_info]: ah_wpa_gen_ptk: wpa_verify_key_mic failed
[auth_fsm]: WPA: 286a:ba44:1de4 WPA_PTK entering state PTKCALCNEGOTIATING
[auth_info]: received EAPOL-Key frame (2/4 Pairwise)
[auth_info]: WPA: Send EAPOL(version=2 secure=0 mic=0 ack=1 install=0 pairwise=8 kde_len=0 keyidx=0 encr=0)
[auth_info]: sending 1/4 msg of 4-Way Handshake
--------------------------------------------------------
Tech data : https://drive.google.com/open?id=0B3ctVg8ubiwUNm5Qdk5GTmZyTGM
---- After first connection (authenticate from cache) log @ AH-016e80 (172.16.1.55) -----
[auth_info]: received EAPOL-Key frame (4/4 Pairwise)
[auth_info]: sending 3/4 msg of 4-Way Handshake
[auth_basic]: STA(286a:ba44:1de4) successfully match PPSK user(ruwanindika+user2@gmail.com)
[auth_info]: wpa_verify_key_mic: data_len 121, sizeof(*hdr) + sizeof(*key) 99
[auth_dump]: PTK - hexdump(len=48): 7a bf ** **
[auth_dump]: PMK - hexdump(len=32): 45 1f ** **
[auth_info]: WPA: PTK derivation - A1=9c5d:1201:6ea4 A2=286a:ba44:1de4
[auth_info]: wpa_derive_ptk: pmk pointer 1101200632, sm->wpa_key_mgmt 2, sm->wpa_auth->addr 9c5d:1201:6ea4 sm->addr 286a:ba44:1de4
[auth_basic]: try PMK stored in roaming cache, username ruwanindika+user2@gmail.com
[auth_fsm]: WPA: 286a:ba44:1de4 WPA_PTK entering state PTKCALCNEGOTIATING
[auth_info]: received EAPOL-Key frame (2/4 Pairwise)
Whats interesting with Aerohive PPSK+IDM is that you can create a PSK (WPA2-Personal) SSID and provide PSK per user. And these PSKs can be authenticated against a PSK list in IDM, so how does this work ?

For this the SSID should be configured in the HiveManager as below,


Lets say you pushed this configuration to 3 access points or more, two of the access points will become IDM proxy. All the access points talk to IDM through the two APs which are elected to be the radsec proxy,

Lets say the client is connecting to the AP with hostname AH-016e80 (172.16.1.55), how does the authentication pkts flow through ? AH-016e80 (172.16.1.55) communicate to AH-0168c0 (172.16.1.56) using RADIUS and AH-0168c0 (172.16.1.56) autheticate the user with IDM using radsec ,
client --- AH-016e80 (172.16.1.55) ----- RADIUS ---- AH-0168c0 (172.16.1.56) --- radsec ----IDM
Pkt capture : https://drive.google.com/open?id=0B3ctVg8ubiwUdmd0T0FKM0Z2S2M
Pkt capture : Client --- AH-016e80 (172.16.1.55)

Pkt capture : AH-016e80 (172.16.1.55) ----- RADIUS ---- AH-0168c0 (172.16.1.56)

Pkt capture : AH-0168c0 (172.16.1.56) --- radsec ----IDM

How would you see this process in Aerohive _debug messages,
_debug auth all
Tech data : https://drive.google.com/open?id=0B3ctVg8ubiwUX0YySndaOElWMnM
---- First connection log @ AH-016e80 (172.16.1.55) -----
[auth_info]: received EAPOL-Key frame (4/4 Pairwise)
[auth_basic]: Query PPSK success for sta 286a:ba44:1de4, username: ruwanindika+user2@gmail.com, session-timeout:
notice ah_auth: authentication OK, username '28-6A-BA-44-1D-E4', service (unknown)
[auth_basic]: Sending PPSK request to external server for sta 286a:ba44:1de4
[auth_info]: ah_wpa_gen_ptk: wpa_verify_key_mic failed
[auth_basic]: try PMK stored in roaming cache, username ruwanindika+user1@gmail.com
[auth_info]: received EAPOL-Key frame (2/4 Pairwise)
[auth_info]: WPA: Send EAPOL(version=2 secure=0 mic=0 ack=1 install=0 pairwise=8 kde_len=0 keyidx=0 encr=0)
[auth_info]: sending 1/4 msg of 4-Way Handshake
--------------------------------------------------------
Tech data : https://drive.google.com/open?id=0B3ctVg8ubiwUNm5Qdk5GTmZyTGM
---- After first connection (authenticate from cache) log @ AH-016e80 (172.16.1.55) -----
[auth_info]: received EAPOL-Key frame (4/4 Pairwise)
[auth_info]: sending 3/4 msg of 4-Way Handshake
[auth_basic]: STA(286a:ba44:1de4) successfully match PPSK user(ruwanindika+user2@gmail.com)
[auth_info]: wpa_verify_key_mic: data_len 121, sizeof(*hdr) + sizeof(*key) 99
[auth_dump]: PTK - hexdump(len=48): 7a bf ** **
[auth_dump]: PMK - hexdump(len=32): 45 1f ** **
[auth_info]: WPA: PTK derivation - A1=9c5d:1201:6ea4 A2=286a:ba44:1de4
[auth_info]: wpa_derive_ptk: pmk pointer 1101200632, sm->wpa_key_mgmt 2, sm->wpa_auth->addr 9c5d:1201:6ea4 sm->addr 286a:ba44:1de4
[auth_basic]: try PMK stored in roaming cache, username ruwanindika+user2@gmail.com
[auth_fsm]: WPA: 286a:ba44:1de4 WPA_PTK entering state PTKCALCNEGOTIATING
[auth_info]: received EAPOL-Key frame (2/4 Pairwise)
[auth_info]: WPA: Send EAPOL(version=2 secure=0 mic=0 ack=1 install=0 pairwise=8 kde_len=0 keyidx=0 encr=0)
[auth_info]: sending 1/4 msg of 4-Way Handshake
--------------------------------------------------------
Friday, September 2, 2016
Aerohive HiveManager not showing the correct wifi client number
I was troubleshooting an issue where the customer was complaining that the client count displayed in the HiveManager is not accurate.
There is one client connected but the HiveManager shows that the client number for that AP is "0"

I though, lets use the "show station" command in the AP to see whether the AP has this client connected, and as you can see the client with mac 286a:ba44:1de4 is connected to the AP,
Aerohive HiveOS running in APs send a traps over CAPWAP to the HiveManager every time a client connect or disconnect, thats how the HiveManager know when a client connect or disconnects to the AP. If you enable capwap trap debug, you can see the trap message,
There is one client connected but the HiveManager shows that the client number for that AP is "0"

I though, lets use the "show station" command in the AP to see whether the AP has this client connected, and as you can see the client with mac 286a:ba44:1de4 is connected to the AP,
-------------------------------------------------------------
AH-0168c0#show station Chan=channel number; Pow=Power in dBm; A-Mode=Authentication mode; Cipher=Encryption mode; A-Time=Associated time; Auth=Authenticated; UPID=User profile Identifier; Phymode=Physical mode; Ifname=wifi0.1, Ifindex=17, SSID=GUEST-PPSK: Mac Addr IP Addr Chan Tx Rate Rx Rate Pow(SNR) -------------- --------------- ---- ------- ------- -------- Mac Addr IP Addr Chan Tx Rate Rx Rate Pow(SNR) -------------- --------------- ---- ------- ------- -------- 286a:ba44:1de4 10.100.0.27 36 6M 65M -48(42) wpa2-psk aes ccmp
After looking in to the logs I figured out the cause of this issue was that the customer had disabled traps over CAPWAP,-------------------------------------------------------------
Aerohive HiveOS running in APs send a traps over CAPWAP to the HiveManager every time a client connect or disconnect, thats how the HiveManager know when a client connect or disconnects to the AP. If you enable capwap trap debug, you can see the trap message,
AH-0168c0#_debug capwap trap
or
AH-0168c0#_debug capwap alldebug trap turned on (0x10)
AH-0168c0#show log buffer
----- client just connected ------
debug capwap: [capwap_trap]: printf capwap send trap buffer:
debug capwap: [capwap_trap]: Send capwap trap sequence number:6, total len:198
debug capwap: [capwap_trap]: total trap len:190
debug capwap: [capwap_trap]: trap management status:0
debug capwap: [capwap_trap]: option55 :, len:0
debug capwap: [capwap_trap]: trap os name :, len:0
debug capwap: [capwap_trap]: trap MBA used:2
debug capwap: [capwap_trap]: trap sta's SNR:-48
debug capwap: [capwap_trap]: trap user profile name :USERMGR, len:7
debug capwap: [capwap_trap]: trap sta's rssi :42
debug capwap: [capwap_trap]: trap ifname :wifi1.1, len:7
debug capwap: [capwap_trap]: trap association time :1472799491
debug capwap: [capwap_trap]: trap bssid:9c5d:1201:68e4
debug capwap: [capwap_trap]: trap client channel :36
debug capwap: [capwap_trap]: trap user profile id :1
debug capwap: [capwap_trap]: trap client vlan id :1
debug capwap: [capwap_trap]: trap mac protocol :3
debug capwap: [capwap_trap]: trap encrypt method :0
debug capwap: [capwap_trap]: trap auth method :5
debug capwap: [capwap_trap]: trap cwp used :2
debug capwap: [capwap_trap]: trap client username :GUEST-PPSK, len:10
debug capwap: [capwap_trap]: trap client username :, len:0
debug capwap: [capwap_trap]: trap client host name :ruwans-ipad, len:11
debug capwap: [capwap_trap]: trap client ip:10.100.0.27
debug capwap: [capwap_trap]: trap object type:1
debug capwap: [capwap_trap]: trap current state:1
debug capwap: [capwap_trap]: trap remote id:286a:ba44:1de4
debug capwap: [capwap_trap]: trap interface index:19
debug capwap: [capwap_trap]: fill trap header len:97
debug capwap: [capwap_trap]: trap code:5
debug capwap: [capwap_trap]: trap description:Station 286a:ba44:1de4 is
authenticated to 9c5d:1201:68e4 thru SSID GUEST-PPSK vid 1, length:84 debug capwap: [capwap_trap]: trap object name:AUTH, length:4 debug capwap: [capwap_trap]: trap type is:4 debug capwap: [capwap_trap]: CAPWAP receive connection change trap! debug capwap: [capwap_trap]: Get trap information, total len:830,
data len 816, trap type:1 internal alarm ID:0xffffffff clear:0
2016-09-02 16:58:12 info ah_auth: Station 286a:ba44:1de4
ip 10.100.0.27 username n/a hostname ruwans-ipad OS Apple iOS, flag = DHCP
----------------------------------
Thursday, September 1, 2016
The free disk space on your HiveManager is insufficient
If you see the error below in HiveManager when trying to generate a backup, you may still be able to generate a backup using the command line interface in the HiveManager. This could be a simpler solution than trying to clear logs and free up space. Try this at your own risk as the backup command through CLI doesn't do a disk space check. Usually the disk space required for a "config only" backup is much lower than what is estimated by the HiveManager,
---
Unable to execute backup operation.
The free disk space on your HiveManager is insufficient:
Required free disk space:49590 M
Actual free disk space:48508 M
---
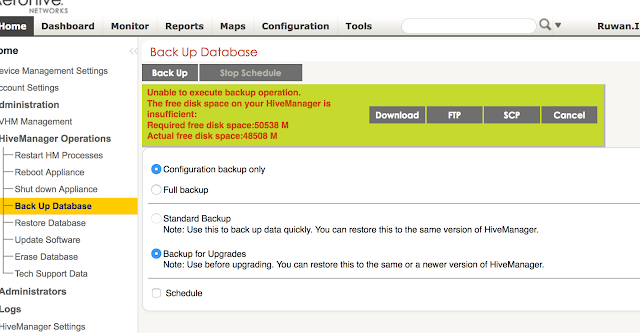
Follow the steps below to by pass the disk space check and generate a backup through the command line interface, select the option to generate a "configuration only" backup,
Follow the menu options , 3 --> 1 --> 7
---
Unable to execute backup operation.
The free disk space on your HiveManager is insufficient:
Required free disk space:49590 M
Actual free disk space:48508 M
---

Follow the steps below to by pass the disk space check and generate a backup through the command line interface, select the option to generate a "configuration only" backup,
Follow the menu options , 3 --> 1 --> 7
1) Network Settings and Tools
2) Display System Information
3) Advanced Product Configuration
4) Reboot Appliance
5) Shut down the System
6) Change CLI Shell Password
7) Logout of shell
Please make a choice:
1) Configure HiveManager
2) Configure VM Params
3) Configure DB Params
4) Back to Parent Menu
Please make a choice:
1) Restart HM Software
2) Shut down HM Software
3) Re-initialize HM Database
4) Change HM Database Settings
5) Restore default HM HTTPS certificate
6) Revert to Previous Version of HM
7) Backup operation
8) Restore operation
9) Get Technical Support
10) Clear HM Logs
11) Clear HiveManager Access Control
12) Change HM Admin Password
13) HA Operations
14) Customize the Common Image
15) Replacement DB sync
16) Display HM Update/Restore Progress
17) Display HM version
18) Back to Parent Menu
Please make a choice:
7
The function backs up the HiveManager database and user files
Backup Content: [1] Configuration backup only; [2] Full backup
Choose a backup option:1
Remote File Server Type: [1] SCP server; [2] FTP server
Choose a remote file server type:2
IP Address/Domain Name:101.187.x.x
[If Enter nothing, will use default value 21] Port:
File Path on the remote file server:/
Login User Name:ftpuser
Login password:
23
=======================================================
Database Backup Parameters
Backup Content: Configuration backup only
Remote File Server Type: TCP server
IP Address/Domain name:Port: 101.187.x.x:21
File Path: /
Do you want to backup the database? [yes | no]
Enter "yes" or "no" :yes
backup progress |==================================================| 100%
FTP progress |=========================
Subscribe to:
Posts (Atom)

