1) Download "AWS Tools for Windows PowerShell" from https://aws.amazon.com/powershell/
2) Install it in a Windows server, in this example I am using Windows 2008 R2.
3) Open Windows power shell and enter the command "Set-ExecutionPolicy RemoteSigned"
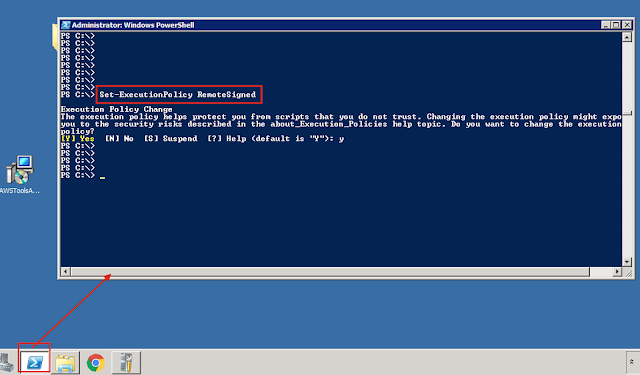
4) Import the module AWSPowerShell
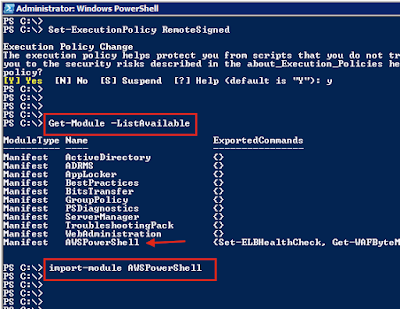
5) Now you can search for the IP address range using command "Get-AWSPublicIpAddressRange"
In this example I want to filter the result by region (eu-west-1) and service (EC2)
Get-AWSPublicIpAddressRange -Region eu-west-1 -Service EC2
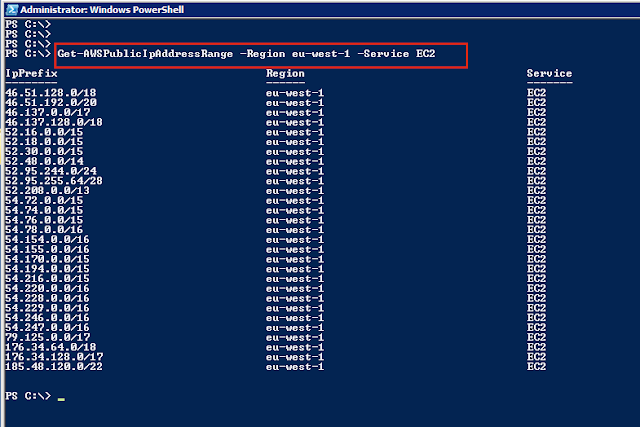
PS C:\> Get-AWSPublicIpAddressRange -Region eu-west-1 -Service EC2
IpPrefix Region Service
-------- ------ -------
46.51.128.0/18 eu-west-1 EC2
46.51.192.0/20 eu-west-1 EC2
46.137.0.0/17 eu-west-1 EC2
46.137.128.0/18 eu-west-1 EC2
52.16.0.0/15 eu-west-1 EC2
52.18.0.0/15 eu-west-1 EC2
52.30.0.0/15 eu-west-1 EC2
52.48.0.0/14 eu-west-1 EC2
52.95.244.0/24 eu-west-1 EC2
52.95.255.64/28 eu-west-1 EC2
52.208.0.0/13 eu-west-1 EC2
54.72.0.0/15 eu-west-1 EC2
54.74.0.0/15 eu-west-1 EC2
54.76.0.0/15 eu-west-1 EC2
54.78.0.0/16 eu-west-1 EC2
54.154.0.0/16 eu-west-1 EC2
54.155.0.0/16 eu-west-1 EC2
54.170.0.0/15 eu-west-1 EC2
54.194.0.0/15 eu-west-1 EC2
54.216.0.0/15 eu-west-1 EC2
54.220.0.0/16 eu-west-1 EC2
54.228.0.0/16 eu-west-1 EC2
54.229.0.0/16 eu-west-1 EC2
54.246.0.0/16 eu-west-1 EC2
54.247.0.0/16 eu-west-1 EC2
79.125.0.0/17 eu-west-1 EC2
176.34.64.0/18 eu-west-1 EC2
176.34.128.0/17 eu-west-1 EC2
185.48.120.0/22 eu-west-1 EC2






















