logging server syslog server IP level debug
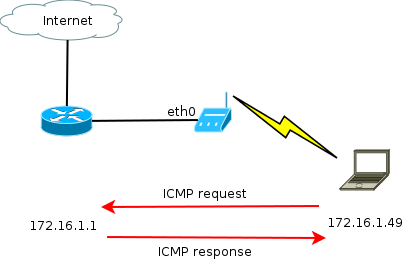
Lets say that you want to see whether the ICMP (ping) request sent by the wifi client is forwarded to the ethernet interface of the AP and to the router,
1) Create a filter that match the pkt you would like to trace
_ff id 1 src-ip 172.16.1.49 dst-ip 172.16.1.1 protocol 1 bidirectional
_ff : is the command to create a filter
id 1 : is the filter ID, you can create several filters with different ID numbers
protocol : UDP:17; TCP:6; ICMP:1
2) Enable forwarding engine debug to print the pkts that match the filter we created in step 1.
_kdebug fe basic
3) Enter the command "clear log all" , ping from wifi client to 172.16.1.1 and the enter the command "show log buffered" to display the pkt trace,
clear log all
ping 172.16.1.1 from the PC
show log buffered
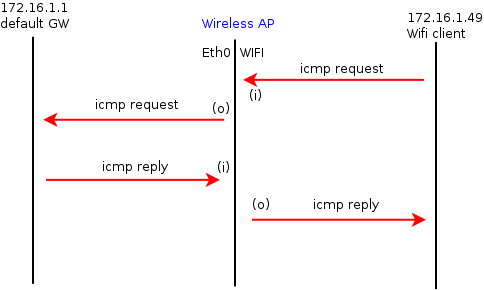
defc3c80::L*: (i) wifi1.1 172.16.1.49->172.16.1.1(60810) ttl(64) icmp-echo-req(35330/2) 84 bytes
--> This line shows that icmp request is coming in from wifi1.1 interface
defc3c80::L*: (o) eth0 172.16.1.49->172.16.1.1(60810) ttl(64) icmp-echo-req(35330/2) 98 bytes
--> This line shows that icmp request was forwarded to ethernet interface
dede0560::L*: (i) eth0 172.16.1.1->172.16.1.49(39153) ttl(64) icmp-echo-reply(35330/2) 84 bytes
-->This line shows that icmp reply came in from ethernet interface
dede0560::L*: (o) wifi1.1 172.16.1.1->172.16.1.49(39153) ttl(64) icmp-echo-reply(35330/2) 98 bytes
--> This line shows that icmp reply was sent to the wifi client via wifi1.1 interface
*** check the time stamps to read the log messages in order
(i) = pkt coming in
(o) = pkt going out
(!) = pkt dropped
No comments:
Post a Comment